
Contents
Types and Advantages of Cyber Security
The present era is surrounded by devices that are connected through the internet. From web banking to government organizations and medical industry, all are associated through the web. With the expansion in the number of web users, there is a substantial increase in the number of cyber-attacks.
Almost every industry in the world today is forming its presence online. However, this information is always at risk, from the potential attacks from the web space. To ward off these possible attacks, implementation of a high security system is important. This is how cyber security as a saver has come into existence. A proper understanding and execution of the process can save the industries of the globe from maximum cyber threats and risks.
Article Summary
Cyber Security has become a concern for companies around the world. The increasing number of cyber crimes is pushing companies to adopt stricter security measures. To adopt the possible cyber security measures, one needs to understand them well first. This article details the importance, types, advantages and disadvantages of Cyber Security. It also provides credible information to the students to clear their concepts and prepare their cyber security assignments.
What is Cyber Security?
In the present time, it is critical to mull over the utilization of viable cyber security components inside various businesses. This step is important to implement as it provides necessary guidelines for securing all the devices connected in a network from potential network assaults. In short Cyber Security is a practice of safeguarding the network, servers, client systems and applications from digital attacks from across the world
Cyber Security as an issue has gained significance due to the increase in number of devices connected to the internet. The cyber attacks when successfully pulled off, can lead to an access, change, or destroy in the sensitive data. This may include money extortion. Thus, it is important to protect all the IT devices from threats of cyberspace and the term is called cyber security.
One such incident took place in August 2015 in which an individual assault of 2.4 million Carphone Warehouse clients. It involved bank details and encrypted card numbers that were influenced by an information penetrate. In a likewise manner, in December 2015, the individual details of around 656,723 clients got traded off. Not just this, the information was made accessible on the dark web which could have caused serious impact on the association. The companies around the world take strong cyber security measures, because leakage of the online data can lead to disruptive consequences.
Why is Cyber Security important?
Cyber security is an important affair because of the amounts of data that is being collected and stored over the internet and servers of the organizations. Several significant militaries, medical, government, corporate, industries and financial organizations depend on the data stored on their servers. This data is one of the most valuable assets of the organization as an organisation takes years to garner this data. Moreover, all the sensitive data is stored on the servers which when compromised can prove to be a crucial threat. It can further have negative consequences as the data might fall prey in the hands of a person or organization with false intentions. Thus, safeguarding the data is important and that feat can only be achieved by implementing the concepts of cyber security.
Types of cyber security attacks
In these days, many companies or individuals are using different types of technology based applications. Some common examples of these applications include smart home, smart office, LinkedIn, Google apps, Twitter etc. There are a number of cyber- attacks which can obstruct the growth of these applications or organization. These can range from Phishing to Vishing to DOS attacks and many others. This section details the type of cyber attacks and information related to it.
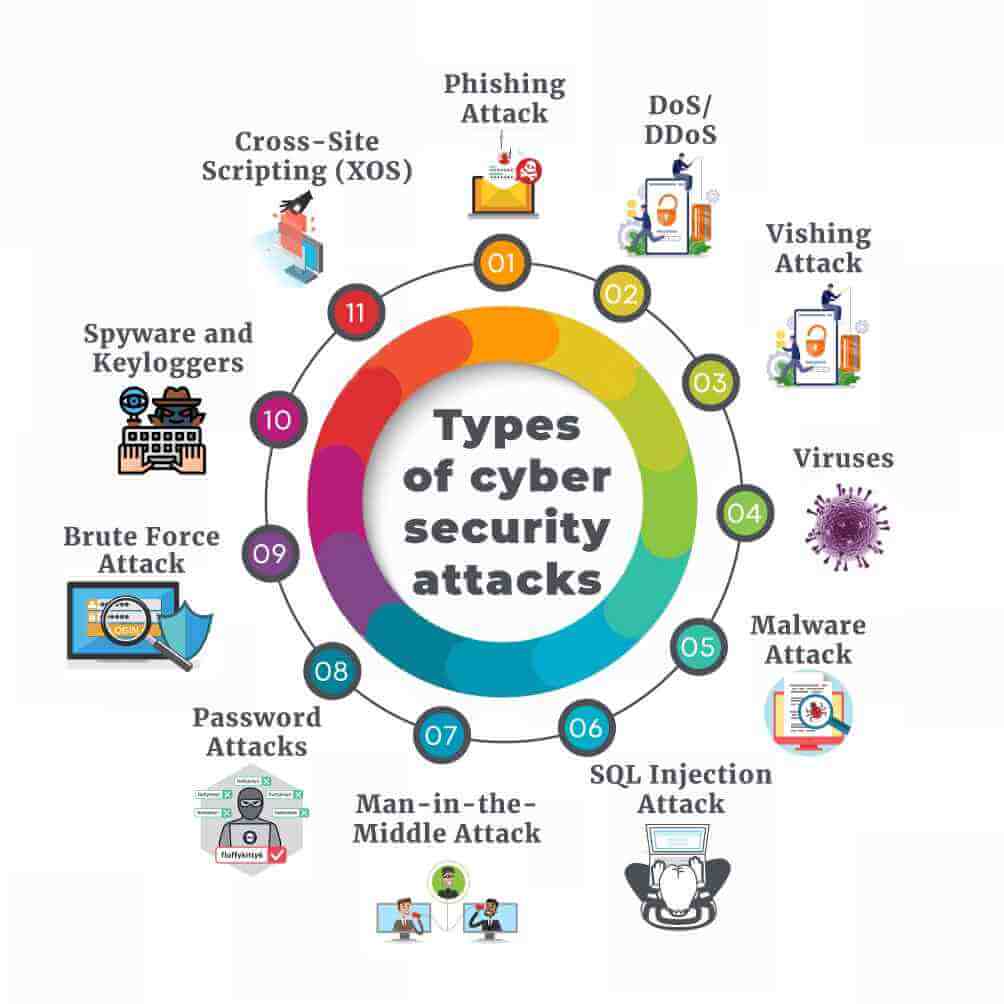
Phishing Attack
Phishing attack is the combination of technical trickery and social engineering in which an attacker sends in an email which imitates as being sent from a trusted source. The phishing attack is done for the purpose of gaining personal information of an individual or persuading them for certain activity. The email might contain the website link which might take input from the user. It further sends the data to the attacker, who might redirect the user to another website which could house malware. Also, emails can itself contain malware attachments which when downloaded can infect the system and reveal sensitive information stored in the computer, thus making it vulnerable. In this attack personal information primarily covers login credentials, credit card numbers or salary information.
Since the end of February 2020 there is a huge increase of 667% in the cases of spear phishing attacks. It has been detected by Barracuda Sentinel. In total 467,825 such attacks were detected out of which 9,116 are COVID-19 related. Whereas, in the month of February only 1,188 such attacks were detected and in the month of January only 137 were detected.
Denial-of-Service (DoS) attack and Distributed Denial-of-Service (DDoS) attack
A denial-of-service attack basically intends to shut down the servers or keep them too busy so that they cannot serve to the requests of its users. In this type of attack, an attacker uses a greater number of machines which continuously flood the server with requests. Its purpose is to make the user too busy to serve these fake requests, that it does not get time to serve the legitimate requests. To carry this out, attackers acquire a huge number of machines by infecting several machines across the world with their malware, so they have access to every machine. In certain instances, when the load is too high, it might crash the servers as well.
However, these attacks do not benefit the attacker by any means as they cannot steal any sensitive and significant information from the server. Rather they can just keep it busy so legitimate users cannot leverage its services. In certain instances, these attacks are also used as a distraction from several other attacks. It is also because when the organization starts focusing on the server being down, they forget to keep up the security of their server.
Attackers using a DDoS attack in recent COVID-19 times, tried to put out the website of the US Department of Health and Human Services (HHS) in order to deprive the citizens of information being posted about the pandemic. However, the website continued to function appropriately although it took a little performance dip, yet it managed to serve the requests under increased load.
Vishing Attack
This is another form of phishing attack in which the attacker makes a phone contact to the customer to get their personal details by claiming themselves to be a genuine user. Most often, these attackers claim themselves to be bank insurance officers for getting the bank details of the user. The assailant utilizes bogus strategies so as to deceive the client for giving his fundamental information to the unauthentic entities. In this kind of phishing assault, the attacker attempts to deceive their clients through SMS messages and fake voice calls.
Viruses
Viruses are the malware programs that contain malicious code that aims to disrupt the normal working of computer systems. Virus has the potential to create its replicas throughout the user’s system for infecting it. Also, it can attach itself to the file of another computer system i.e. spreading itself. After corrupting a user's file, it steals all the information contained in the file. And, it might be possible that the file may contain user’s bank account details which could be harmed by the malicious hacker. Virus cannot work without a host program as it is the one which looks for other files on the system which are uninfected, so as to steal the information contained in such files.
Malware Attack
Malware attack is basically done using malicious code which can destroy the whole network including the server and its clients. It provides attackers the access to the sensitive information and control over the machine. It is more dangerous because it can sit in the network without being traced for prolonged durations, thus sniffing data from the packets, and causing internal damage to the information by leaking their information. It is even considered as lethal, as it can imitate like a legitimate code and self-propagates through the network, thus spreading to all the devices connected over the network.
On April 20, 2020, a US IT firm was attacked by Maze ransomware which encrypted their all data and sent email to the customers which included an IP address and a file. It locked the organization out of their systems and encrypted the data. Also, it stole the data of the organization, thus privacy of customer data got compromised. It could not be decrypted and the organization could not get access until it paid the asked sum of ransom.
SQL Injection Attack
As suggested by the name, it is the attack on database-based websites. When SQL injection is carried out successfully, it provides the attacker the access to sensitive information such as login credentials, payment information and personal information of clients along with the staff members. This attack is carried out using the SQL commands which are inserted into the database to run certain operations in the database. This can benefit an attacker by a huge margin as they can steal the information and may sell the information for huge profits or might exploit the leak information over the internet. In certain cases, attackers also delete the data, causing much significant damage to the organization.
In 2016, a SQL Injection attack was carried off at Illinois Board of Elections which compromised the data of 200,000 citizens. As a result, the server was taken down for 10 days in order to repair the server and fix the vulnerabilities and flaws.
Man-in-the-Middle Attack
It is a type of cybersecurity breach in which an attacker eavesdrops the packet transfer between a client and a server and each of them knows that their conversations are being listened to. This enables an attacker to gain access to certain information which otherwise would not have been available. Also, an attacker can capture and modify the packet before sending it towards the destination.
A logistics organization from Mumbai, India fell prey to an unidentified attacker and allegedly lost $16,000. The attacker used MITM technique to sniff the payment the company was about to receive, by hacking their official account.
Password Attacks
These involve hacking attempts by malicious hackers for getting unauthorized access to the organizational security system. In order to gain access, the hackers may use some password cracking or security scanner tools. Most often, these password cracking tools are used in the login procedures in order to get an unauthentic pass to the user’s account for stealing the user's credential and other information.
Brute Force Attack
Brute force attack is a networking attack in which an attacker over-powers the system and tries to gain access to the system by force i.e. trying all the possible methods and passwords. The procedure is carried out until a correct access key is found and access is gained to the account. It is used in collaboration with a dictionary software which enables it to try thousands of dictionary words while making all the possible combinations. However, the attack is not quite efficient, as in case the other party gets to know about any such brute forcing, they can tighten their security in the meantime, thus defying the attack.
TaoBao, a venture of Alibaba Group fell prey to a massive brute force attack, leading to breach of up to 21 million accounts. The attackers were identified to use the database of 99 million accounts. This resulted in the company to compromise 1 out of every 5 accounts i.e. 10.6 million accounts.
Spyware and Keyloggers
Spyware is a kind of malware attack that aims at identifying the activities that are held in the victim’s computer system. On the other hand, there is another malware named Keyloggers which aims to record all the keystrokes pressed by victims. This may include details regarding password, login, bank account or other crucial information which might get compromised with this backend recording program. Basically, these spywares and Keyloggers work by entering into the user’s system after the user installs or downloads any corrupted file from malicious websites. Since, these spyware and keylogger programs are already present in the user's system. Therefore, it might result in sharing this crucial information along with the user's browser history to the malicious hacker who might be controlling all this activity at his end. Further, the hacker may either sell this information to a third party vendor. Also, he can use the customer information for making false transactions through his bank account details. Further, it might also be possible that the hacker may leak out this data on the dark web which could be exploited by anyone.
Cross-Site Scripting (XOS)
The attack is an injection breach, in which reputed websites are taken as hosts and malicious scripts are sent via them, as people usually trust the content from these websites. This feat is achieved by attaching the malicious code with the dynamic content of the website. Here, the target browser executes JavaScript code snippets which are then sent to the victim’s browser. It happens due to the active vulnerabilities in the website of the host.
In 2018, British Airways suffered a data breach which involved a cross-site scripting attack. It impacted almost 380,000 booking transactions between August 21 till the month of September. The breach affected both mobile app and website users.
Advantages/benefits of cyber security
Cyber security as an exercise is highly advantageous. along with saving the users from possible cyber attacks it also warns it from potential risks. The following is a list of cyber security benefits.
- It protects the personal and sensitive data of an individual and organizations from being stolen.
- The main advantage that could be achieved with the utilization of these effective cyber-security mechanisms is the protection of networks from various false nodes which try to gain unauthorized access to the network.
- The most important aspect is that it enhances the security of the system in cyberspace.
- It eliminates the risk of computers being hacked, thus mitigating the risk of system freezes and crashes
- It enhances overall security mechanisms of the business with the use of an improved information framework and results in smooth business management activities.
- It identifies the vulnerabilities and weak entities that can aid an attacker to attack the system or the server. These vulnerabilities upon identification can help the teams to secure the systems in order to prevent such attacks from happening.
- It protects the system against spyware, virus, malicious codes, trojan horses, worms, and several other unwanted infectious programs.
- It gives the much-wanted privacy to a user and the organizations as it protects their personal information which might hurt their sentiments if leaked.
- It is beneficial for mental health as it induces a sense of security in an individual
- Enhanced stakeholder support in the effective security mechanisms applied in the business.
- With the incorporation of effective cyber security mechanisms, the stolen data could be easily restored.
- More reliable company credentials with a compelling security framework in the business.

If you lack time, then we can lend our expert services to you!
We, at Assignmenthelp4me, have the most efficient academic writers.
The complexities of Cyber Security assignments do require a helping hand to dive through. We, at Assignmenthelp4me, endeavor to become one for you. It is much possible because of our years long experience in the field of academic writing. Along with this our professional writers from the relative subject field, makes assignment writing super easy for us. All this together facilitates us to give your assignment solutions back in time and drafted with high quality writing standards.
Disadvantages/challenges of cyber security
So as to give a powerful digital security component inside an association, it is required to adjust all its endeavours through its information system. Following are some of the potential challenges which the organization might encounter while incorporation of effective cyber security mechanisms within the organization. These are clarified as follows:
- Cyber security can be a costly affair; as highly trained professionals are required.
- Latest security patches must be updated regularly with the latest security definitions, which is difficult to keep up with.
- In order to keep the system secure, a firewall must be configured appropriately, but it is a difficult task. As several security measures must be implemented appropriately, if done incorrectly it can even block legitimate users out of the system.
- Providing remote access is an essential element in the business, yet it can become a loophole for the business as the attacker may gain unauthorized access through this network.
- AI expansion is a challenge for cybersecurity, as robots are being developed in a manner to protect cyber-attacks from happening.
- Interconnectedness with the advent of IoT is a challenge for cybersecurity, as if security of one device is compromised, it can easily self-replicate to all the connected devices.
- Identity management could be another issue that the business may confront as it might happen that the business has no clear access provisions inside the business due to which anybody can have access to the system.
- The most challenging factor in cyber security is the regularly advancing nature of security risks. Due to this, the association may not be able to adopt any proactive strategies for shielding its information from different digital ambushes.
Cyber Security Essay (Sample)
Cyber Security has become a significant viewpoint for the business, medical, government and different associations. It is due to the fact that these associations accumulate and store unprecedented amounts of information on the computers and other devices. A significant portion of this information may contain some delicate data, for example, licensed property or money related or personal information of the client. If the intruder successfully manages to gain unauthorized access to the organization’s system then this highly sensitive data may get traded off which may provoke some serious implications on the association.
The associations transmit their information to different associations taking into account business forms and, cyber-security depicts certain principles or rules for shielding the data and framework from different kinds of network assaults. This prevents the organizational information from getting shared or being compromised at the hands of the attacker. With the expansion in the number of digital assaults, different associations and organizations try to embrace viable cyber security techniques for protecting their authoritative data. In order to safeguard the business operations from unnecessary interruptions, there are various ways with which associations can secure their information from the expanding cyber-attacks. This could be accomplished by facilitating data security, system and application security inside the association's framework. Through the data framework, the organization aims to secure user’s highly sensitive data from unauthentic access, identity theft. This could be done through user authentication and encryption techniques.
Further, network security flourishes to ensure ease of use, data integrity and security of a network along with various devices connected in it. When a particular network is secured, the potential dangers get obstructed from the expansion of unauthentic access on that organization.
Additionally, Application security tries to shield programming applications from specific vulnerabilities or flaws which may give a passage door to the hacker for getting unapproved access to the information. Other than this, end user protection can be seen as a significant angle in the space of digital security. As, it is a person who may accidently get trapped in the malware or another type of digital danger. In this way, so as to secure their frameworks from such malwares or different assaults, the end client must utilize powerful encryption procedures from saving the information being shared on to the framework. Other than this, the clients can utilize successful software scanners for their computers so as to check malicious code. When this code is checked, diverse security programs could be applied for clearing out all the deformities in the framework; henceforth shielding the framework from network assaults.
FAQ
What is cyber security and its types?
Cyber security is a practise that refers to safeguarding the privacy and security of computers, mobiles, servers and other electronic devices from unauthorized and threatening attacks. The various types of cyberattacks include password attacks, phishing attacks, drive-by attacks, XSS attack, MiTM attack among many others.
What are advantages of cyber security?
One of the biggest advantages of cyber security is that it protects the system of the user from unwanted threats and attacks in the digital environment. It also helps the businesses to grow in a smooth and a threat free environment.
What is the best cyber security?
There are a number of software which provide high security from malicious software. SiteLock, Teramind, WebTitan, Firewalls, Tines, ThreatAdvice, Acunetix are few of the best software in the industry.
