
Contents
An illustration of communication protocols and its types
What are Communication Protocols?
For any data transmission within a network, it is imperative to consider an effective protocol which defines certain rules, conventions or guidelines. It is with the help of such protocol, a secure communication can be established amongst different network nodes for the exchange of data. To explain further, protocols are defined as separate layers where each layer is specifically designed to perform a specific task. For a protocol specification, it is significant to specify its main operation which needs to be formed along with the technique using which protocol will function.
Article Summary
The increasing need of a safe and secure data transmission has given rise to the importance to understand communication protocols. Moreover, the proper identification of the type and rules, allows the user or an organisation to generate even better results. Also, the right understanding is important due to the variation in the types of communication protocols. This article provides a detailed introduction to communication protocols, its importance and types.
A protocol specification mainly comprises three different components which incorporate- header section containing the detailed information of the protocol, clear definition of technique using which the protocol would be implemented along with services performed by its separate layers. Communication protocols can be viewed as a set of guidelines that enable the user to send a block of data from one location to another. For effective data transmission, network nodes make use of clear formats. The usage of communication protocols assures enhanced security to network communication among communicating network nodes.
Different types of communication protocols define certain rules for establishing communication between two different network nodes. These incorporate- ‘Transmission Control Protocol, User Datagram Protocol, File Transfer Protocol and even many more are present. The appropriate communication protocol is used in the network depending upon the network requirements. The communication protocols are fundamentally used for transmitting data in analog as well as digital communications. Additionally, synchronization could be assured with the utilization of such effective communication protocol. This is because of error handling techniques and semantics that are used in protocols. Communication protocols can be incorporated either in hardware or software elements and are mainly used in the digital communications for communication among the network nodes.
The assignment load on you is generally high. In such a situation, you yearn for someone to help you out. We are the perfect solution for your yearning as we at Assignmenthelp4me, have the best academic writers with us. Our team of professionals help you sail through your burden of assignments. You just need to place an order for whichever assignment type, whether it is Communication protocol assignment or database assignment. Our experts make sure to help you in the best possible way.
Types of Network/Communication protocols
Clear combination standards are a necessity for effective communication. These standards define certain rules that are followed for establishing a secure connection among various devices in the network. Also, these administer how a specific technology is to be utilized in the communication. There are various sorts of network protocols available which enable different nodes to communicate across the network. Although each protocol is assigned with specific port numbers as there are a total of 65535 TCP and UDP ports. For instance, FTP protocol uses 20/21 port number one for sending the data and one for receiving the data. These network protocols include the following:
Transmission Control Protocol
It is the most widely used transmission protocol which is actualised for establishing a connection between two end nodes connected within a network. TCP protocol divides a data packet or message into a small number of packets which are transmitted from source location to the destination. Once all data packets are assembled at the destination, they are amalgamated in their original form so that data can be accessed by the receiver. Moreover, TCP protocol is a connection-oriented network protocol that builds a connection between the network nodes for transmitting the data over the network.
User Datagram Protocol
UDP is a network-based communication protocol which is an alternative to the TCP protocol as it establishes a network with reduced latency among various applications. It is a connectionless protocol that does not have any well-defined path or ending point. Rather it is a simple network protocol that is used for streaming data.
File Transfer Protocol
FTP protocol mainly functions by transferring the files from one system to another. The type of files to be transferred under this protocol generally include- text files, program files, documents, images and many other kinds of file.
Internet Protocol
IP can be viewed as addressing protocol which is most often used with TCP protocol as when the data packets are transferred from source to destination, they are assembled using the IP addresses of each data packet. TCP/IP together becomes the most powerful network protocol allowing various network nodes in the network.
Simple Mail Transfer Protocol
SMTP is a simple network protocol which is intended to send and circulate outgoing mails. All mailing systems use SMTP protocol in order to provide mailing services to their clients.
Telnet
This network protocol allows different network nodes to establish a connection with each other. By the term connection, it could be inferred that remote login is established where the client node sends a request for the access to the remote system. Once the access grant is approved, a connection is built between a local computer and a remote system.
Hyper-Text Transfer Protocol
HTTP is intended for moving a hypertext between two or more frameworks. HTML tags are taken into consideration for building such hyperlinks. And it is imperative to note that hyperlinks can be in any form; it may be a normal text or an image. This protocol follows the client-server approach where the client node sends a request to the server for establishing a connection. On the other side, the receiver after receiving a connection request acknowledges the request sent by the sender node and responds in the required manner.
Hyper-Text Transfer Protocol Secure
This standard protocol aims at providing additional security to the network nodes that are sharing a connection over the network. Two systems are connected and the main purpose of this HTTPS protocol is to secure the communication channel between two nodes. This security could be achieved with the utilization of encryption algorithms which convert the data in encrypted format. It further secures the data packets from getting compromised by malicious hackers. In this manner, all data packets which are transmitted from one system to another are secured from various kinds of network assaults.
Importance of Communication Protocols
In essence, there exists an essential need for communication protocols as these protocols aid in establishing a connection with two or more users without facing any difficulty. These protocols are used in computer networks as well as telecommunication where appropriate rules are implemented to transmit information from origin to destination. Let us understand the importance of protocols with an example. The most crucial protocols in networking are Transmission Control Protocol and User datagram protocol. (TCP and UDP). Both protocols consist of 65535 protocols so that multiple services are provided to the users. Moreover, in future also, the significance of communication protocols will increase by several folds.
Electronic Communication Protocols
Apart from these network protocols, certain communication protocols are used for transferring blocks of data from one single node to another node within the same network. These communication protocols work in a layered manner in which there are different layers and each of these layers are designed to perform a specific task. Most often, the use of OSI layer is taken into consideration. The network protocols are classified into two main categories which embrace the following:
Inter System Protocol and its Representation
This protocol is used to facilitate communication amid different devices within a network. And the communication is performed by using an inter bus within the system. A connection established through interconnect system can be depicted as follows:
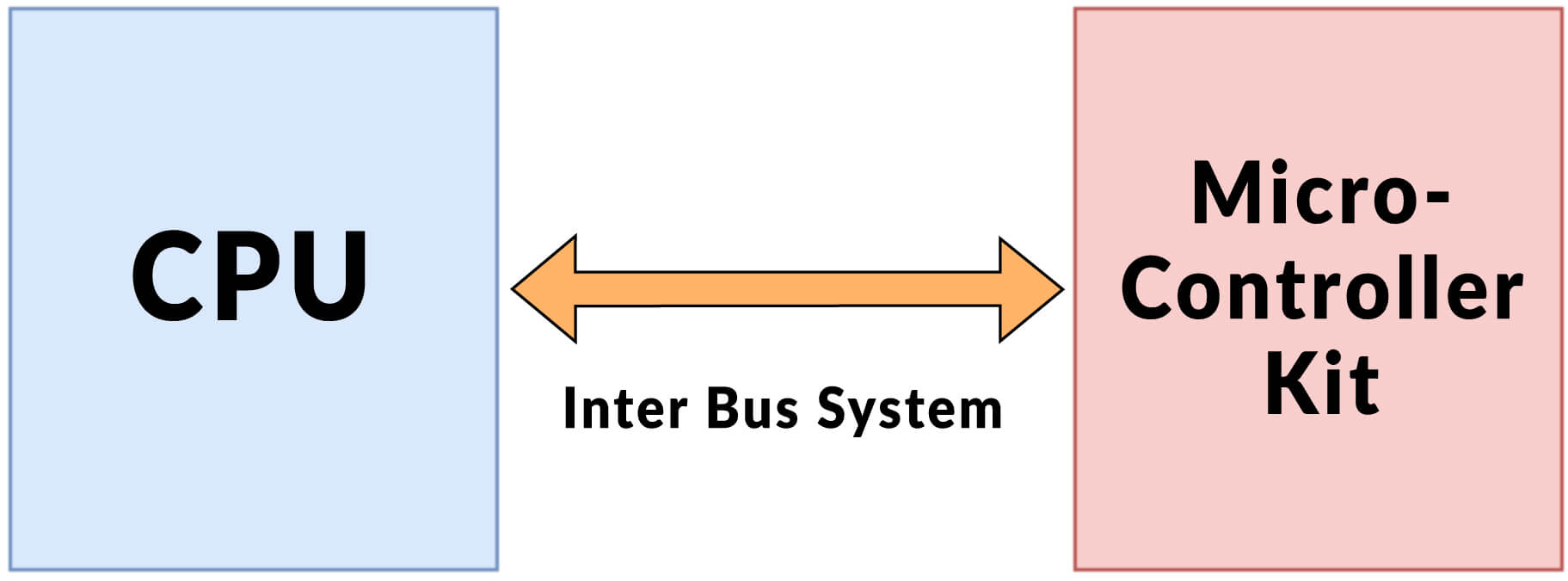
Categorization of Inter System Protocol
The inter-system protocol is further categorized into three different protocols which incorporate the following:
| UART Protocol | USART Protocol | USB Protocol |
|---|---|---|
| UART, abbreviated for Universal Asynchronous Transmitter and Receiver is a standard communication half-duplex protocol that enables serial communication among network nodes. It makes use of wired protocols for transferring and receiving the data in a serial order. Also, it is important to note that serial communication is done by sending bit by bit data. For instance- Walkie-Talkie. | USART, short for Universal Synchronous and Asynchronous Transmitter and Receiver, is a full-duplex communication protocol that enables serial communication. The functioning of this protocol is almost similar to the UART protocol except for the fact that the data is transmitted and received in byte by byte manner. Also, a clock pulse is followed throughout the communication procedure. For instance- Telecommunications. | USB protocol i.e. Universal Serial Bus is a serial communication-based protocol that enables communication to the peripherals of the system. In this type of protocol, there is a connection between the client and host along with peripheral devices attached to the system. This protocol works by installing various driver software on the system. The USB devices can be used to transfer the data onto the system bus without involving any request from the sender to the host system. For instance- pen drive. |
Intra System Protocol and its Representation
This protocol establishes a connection between different network nodes using a circuit board. With the utilization of these intra systems protocol, the circuit complexity along with energy consumption could be increased to another level. Eventually, it reduces the overall cost for providing adequate power consumption. This is a highly secure system for gaining access to the data. Communication through intra system protocol can be displayed in the underneath section as follows:
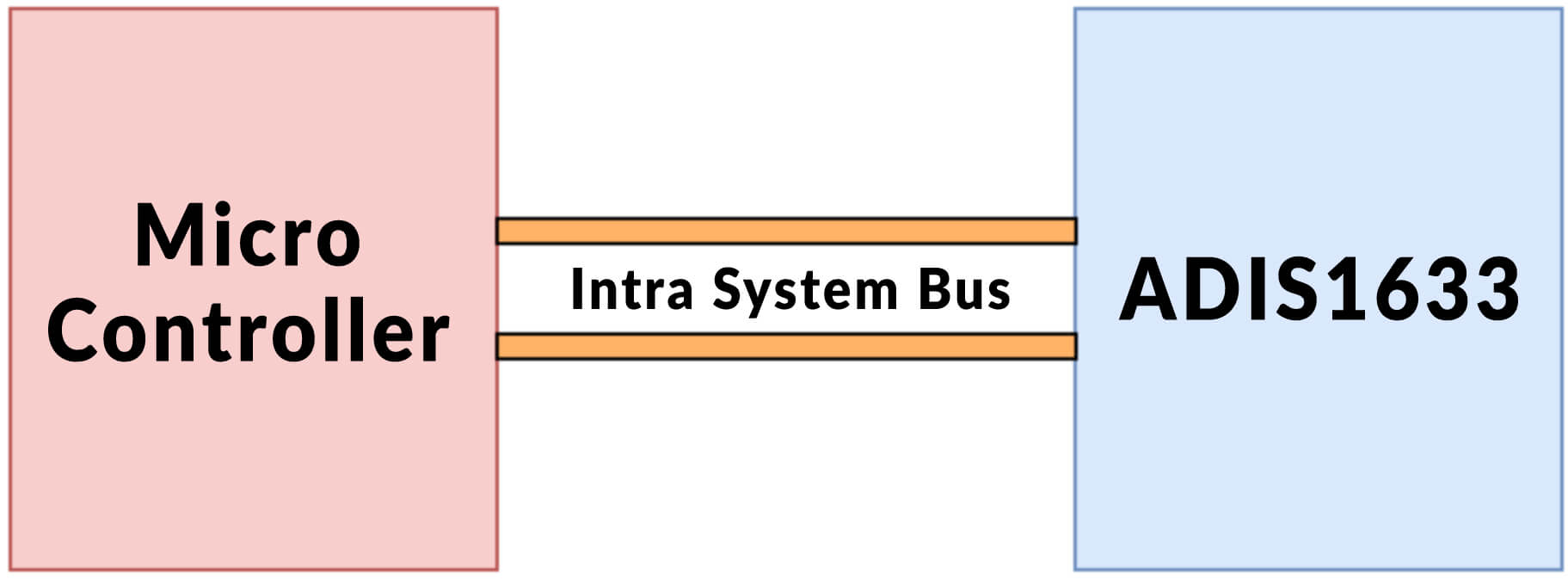
Categorization of Intra System Protocol
The classification of this effective protocol can be shown as follows:
| I2C Protocol | SPI Protocol | CAN Protocol |
|---|---|---|
| Inter Integrated Circuit makes use of two cable wires for building connection between peripheral devices of a system along with the microcontroller. The two wires that are (bi-directional) required for the connection contains information which is to be shared between several devices. This effective protocol was brought up by Philips. This protocol can be seen as a half-duplex that provides synchronization between different devices. | SPI which is short for serial peripheral interface is a standard serial (full-duplex) communication protocol which makes use of 4 wires for connection establishment. The SPI protocol was launched by Motorola which included wire protocols that incorporate- SQL, SS, Q/MOSI and MIS. This enables a connection between the master devices along with slave devices in the network. The master will select only one slave at a time for connection. | CAN abbreviated for Controller Area network is a serial communication protocol that requires two cable wires for connection build up. These cable wires are known as CAN high denoted by (H+) and CAN low which is denoted using (H-). This effective standards serial communication protocol was launched by a person named Robert Bosch. And it works using message based communication protocol. |
Some Prominent Network Transmission Protocols
Apart from the above defined protocols, there exists many other protocols that provide assistance to the primary protocols for enhanced functioning. These protocols are elaborated in the underneath section as follows:
Address Resolution Protocol
Address Resolution Protocol is a standard communication protocol which is mainly used for identifying the address layer, for instance- MAC address of a particular system. This relative address must be related to the address of the internet layer which could possibly be IPv4. This protocol is used along with the Internet Protocol for discovering the address layer.
Simple Network Management Protocol
The main purpose of this internet protocol is to gather and manage all the data regarding various devices connected in the network (which could either be LAN i.e. local area network or WAN i.e. wide area network). Once the information is gathered, this information is modified so as to check the working of the devices in the IP network. The usage of SNMP protocol is mainly considered for monitoring the network devices connected in the IP network. Also, it is used to transform all the devices connected in the network in a standard language. This makes it a lot easier to transmit data onto the network along with easy management of network devices.
Assignment loads are often tough to explain, especially when it comes to technical assignments. One of such time taking college assignments is the Communication Protocol assignment. Thus, to relieve your load, we are always there. Our specialists endeavour to serve each of your assignment requests with high precision and accuracy. Moreover, we make sure that all your communication protocol assignments are solved in time and as per your college guidelines.
Dynamic Host Configuration Protocol
This protocol helps in configuration of all the network devices in the network and thus facilitating them to use services provided in the network. These services may include- DNS or TCP protocol. Basically, DHCP protocol works by assigning dynamic addresses to the network nodes in order to connect them to the network for accessing various network services.
Layer Two Tunneling Protocol
This protocol is mainly used by the internet service providers with a view to enable the clients with VPN i.e. Virtual Private Network capabilities to gain access to private networks. The working of this L2LP protocol is somewhat similar to the data link layer that is a part of the effective OSI model. The primary purpose served by this effective protocol is to minimize the network traffic in an effective manner. Further, this protocol is capable of handling almost L2 data format over the Internet Protocol which makes it very effective.
Session Initiation Protocol
This protocol is widely used in the session applications where it manages the overall operations held in the sessions. It includes initiation, maintenance and the release of these sessions held through different messaging applications. Not only this, the protocol specifies a standard format for transferring data over the network. The SIP protocol is the one behind the effective communication held over the messaging applications as it enables its users to convey voice messages and other files over the web. It is one of the simplest and cheapest methods for communicating over the internet. The working a SIP protocol can be depicted as follows:
Interactive Mail Access Protocol
IMAP, which is abbreviated for Interactive Mail Access Protocol is an effective protocol which is mainly used for defining access to the mail by the user. This mail access protocol is quite similar to the POP3 protocol. However, IMAP inhibits more functionalities and is more complex than the POP3 mail access protocol. With this protocol, the user can have access to the mail and make necessary modifications to the mailbox of the client. IMAP protocol runs effectively on port 143 and was developed to deal with issues that arise with the utilization of POP3 protocol.
Trivial File Transfer Protocol
TFTP protocol works in a similar manner as the FTP protocol as it is mainly used to transfer files from one location to another. However, the TFTP protocol works by empowering the client to get to the document which is stored at a remote area. This file stored at a remote area is facilitated by a remote server giving access to the clients. This convention is basically utilized in the underlying phases of hubs booting from a LAN. This protocol utilizes UDP protocol for moving information starting with one area then onto the next.
Communication Protocol is therefore very important to be first selected, initiated and then implemented in the right manner. To use the right communication protocol, it is important to understand the various mechanisms and protocols. Thus, an organisation can ensure a smooth communication management system with the correct understanding and utilization of the multiple communication protocols.
FAQ
Which is basic communication protocol?
The basic communication protocol is the Transmission Control Protocol. It is with the help of this protocol that a network conversation is established and maintained and then the data can be exchanged by application programs.
What are the types of communication protocols?
There are various types of communication protocols. The list includes Transmission Control Protocol, Internet Control Message Protocol, File Transfer Protocol, Hypertext Transfer Protocol and User Datagram Protocol, among many others.
Why are communication protocols important?
Communication protocols help varied network devices communicate with each other. These assist in the transmission of analog and digital signals and various files and data processes from one device to another.
